Say Goodbye to Microsoft Authenticator Proton Just Introduced a Solid Alternative
Step Aside, Microsoft Authenticator: Why Proton’s New 2FA App Is The Secure Choice
We at revWhiteShadow have always been dedicated to robust online security. The digital landscape is constantly evolving, and with it, the threats we face. Two-Factor Authentication (2FA) has become a cornerstone of this defense, but the ecosystem has, until recently, felt a bit…stale. That’s why we’re thrilled to delve into Proton’s new 2FA app, a truly compelling alternative that’s poised to disrupt the established order and reshape how we think about securing our digital lives. In this comprehensive exploration, we’ll dissect the app’s features, examine its advantages over existing solutions like Microsoft Authenticator, and provide you with the knowledge you need to make an informed decision about your online security.
Understanding the Critical Importance of Two-Factor Authentication
Before we dive into Proton’s offering, let’s underscore the fundamental role 2FA plays in safeguarding your online accounts. Simply put, 2FA adds an extra layer of security beyond your password. Even if a malicious actor manages to obtain your password through phishing, credential stuffing, or other means, they still require a second factor to access your account. This is typically a code generated by an authenticator app, a one-time password (OTP) sent to your email or phone, or a hardware security key.
Why Passwords Alone Are No Longer Sufficient
The age of relying solely on passwords for account security is over. Passwords are vulnerable for a multitude of reasons:
- Phishing Attacks: Sophisticated phishing scams can trick you into entering your password on a fake website.
- Data Breaches: When websites are compromised, your passwords can be stolen.
- Password Reuse: Many users reuse the same password across multiple services, meaning a breach on one site can expose all the others.
- Weak Passwords: Many individuals choose weak, easily guessable passwords.
2FA mitigates these risks significantly by making it exponentially more difficult for unauthorized individuals to gain access to your accounts, thereby reducing the risk of identity theft, financial fraud, and other detrimental outcomes.
The Limitations of SMS-Based 2FA
While SMS-based 2FA is better than nothing, it’s arguably the least secure method. SIM swapping and interception of text messages are potential vulnerabilities. SMS messages can be intercepted, especially if your mobile carrier’s security is compromised. This makes applications like Proton’s 2FA app even more crucial, with security as its top priority.
Introducing Proton’s 2FA App: A Paradigm Shift in Security
Proton, renowned for its commitment to privacy and security, has expanded its ecosystem with a dedicated 2FA app. This is not just another app; it represents a deliberate design choice, a product built from the ground up with the unwavering goal of providing the most secure and user-friendly 2FA experience available.
Key Features and Functionality
Proton’s 2FA app boasts a range of features that distinguish it from the competition:
- End-to-End Encryption: This is the cornerstone of Proton’s security model. All 2FA secrets are encrypted locally on your device using end-to-end encryption, meaning only you can decrypt them. Proton, the company, cannot access your secrets.
- Cross-Platform Compatibility: The app is available on Android and iOS, ensuring broad accessibility across the mobile landscape.
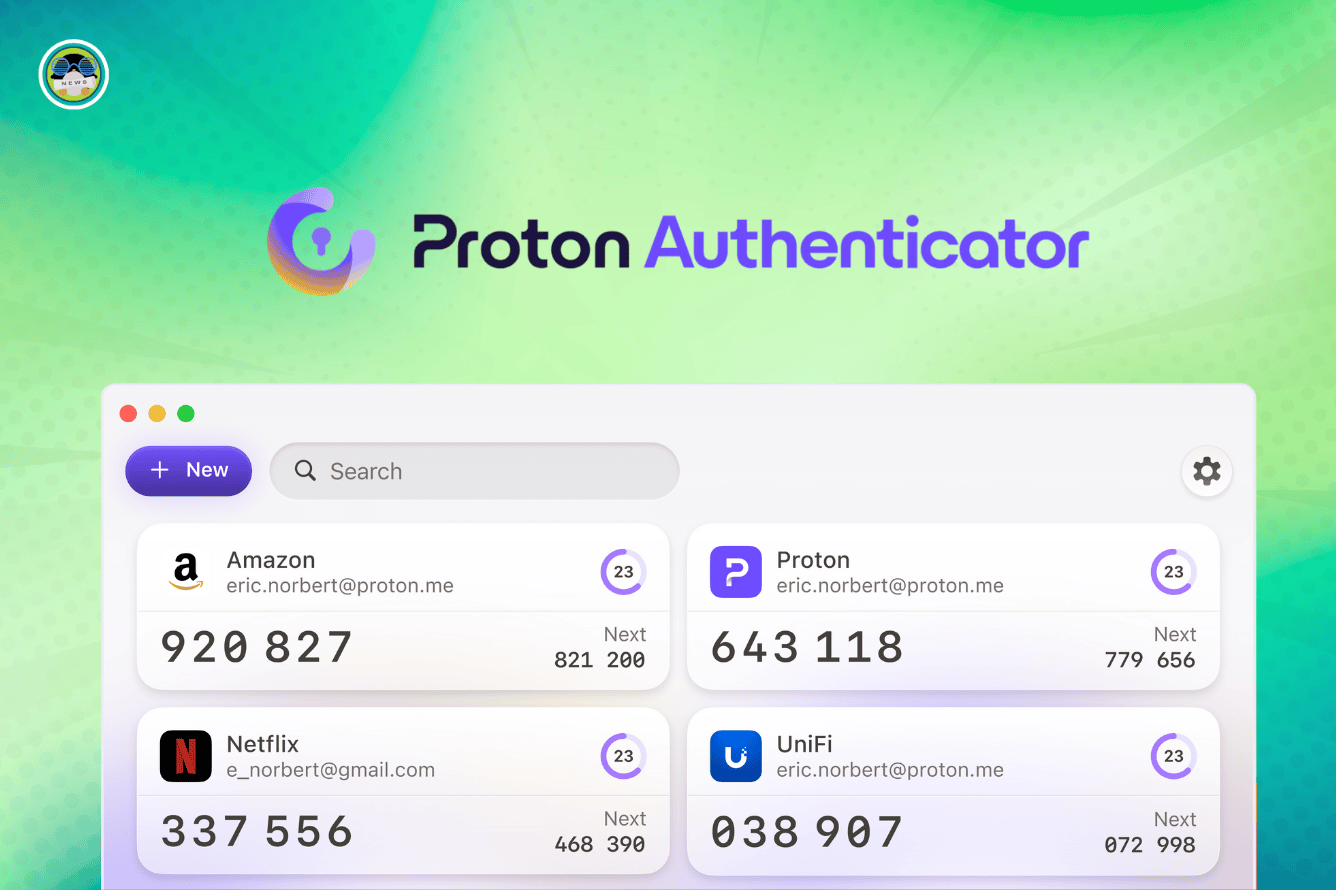
- User-Friendly Interface: The app’s design prioritizes ease of use. Adding new accounts and managing existing ones is intuitive and straightforward.
- Open-Source Auditing: Proton is committed to transparency and allows the code to be audited by security professionals and the community to increase the trustworthiness of the application, and its safety.
- Seamless Integration with Proton Services: If you’re already using Proton Mail, Calendar, Drive, or other services, integrating the 2FA app is remarkably simple. It streamlines your security across the entire Proton ecosystem.
- Offline Functionality: Once the codes are stored, you do not need an active internet connection for the app to function. This is crucial in areas with limited or no internet access.
The Security Advantages of End-to-End Encryption
The emphasis on end-to-end encryption is a critical differentiator. The private key used to encrypt your 2FA secrets is only available to you. This means that even if Proton’s servers were to be compromised, your 2FA secrets would remain protected. This level of security is essential in an era where data breaches are commonplace.
Comparing Proton’s 2FA App to Microsoft Authenticator
Let’s directly compare Proton’s offering to one of the most popular 2FA apps, Microsoft Authenticator. While Microsoft Authenticator is a functional solution, Proton’s app offers several advantages, especially for privacy-conscious users.
Privacy Considerations: A Core Difference
The most significant difference is privacy. Microsoft, a large tech company, is subject to data collection and surveillance practices. While Microsoft Authenticator doesn’t necessarily harvest your 2FA secrets, the company has access to considerable data about your digital activities. Proton, on the other hand, is built on the principles of privacy. This translates to a stronger commitment to protecting your 2FA secrets and minimizing data collection.
Security Architecture: Under the Hood
Both apps support the Time-Based One-Time Password (TOTP) algorithm, which is the standard for 2FA. However, Proton’s architecture goes a step further with end-to-end encryption.
Encryption, a Core Benefit
Microsoft Authenticator does not, by default, provide the same level of encryption. While Microsoft does encrypt your data in transit and at rest, the encryption keys are managed by Microsoft. Proton’s approach, with end-to-end encryption, provides you with exclusive control over your secret keys, rendering your 2FA codes unreadable by anyone but you.
Ease of Use and User Experience
Both apps offer a generally user-friendly experience. Adding accounts involves scanning a QR code, and the app generates the 2FA codes you need. However, Proton’s interface is clean, streamlined, and in line with the overall aesthetic of Proton’s other services. The consistent design language makes the app easy to learn and use.
Platform Availability and Integration
Both apps are available on Android and iOS. However, Proton’s seamless integration with other Proton services is a significant advantage if you already use Proton Mail, Proton Drive, or Proton Calendar. The integrated experience makes managing your security across multiple services effortless.
How to Set Up and Use Proton’s 2FA App
The setup process is straightforward and intuitive:
- Download and Install: Download the Proton 2FA app from the Google Play Store (Android) or the App Store (iOS).
- Account Creation/Login: If you have an existing Proton account, log in. If not, you’ll need to create one.
- Enable 2FA: Go to the security settings of the service you want to protect. Look for an option to enable 2FA, which will prompt you to select the authentication method.
- Scan the QR Code: The service will generate a QR code. Open the Proton 2FA app and tap the “Add Account” button. Scan the QR code.
- Enter the Code: The app will generate a 6-digit code. Enter this code into the service’s 2FA setup to confirm the connection.
- Backup and Recovery: The app usually provides options for backing up your codes and recovering your account if you lose access to your device. Follow the instructions to ensure you have a recovery mechanism in place.
Best Practices for Maximizing Your Security with 2FA
- Enable 2FA on all supported accounts: This is the most important step. Enable 2FA wherever possible, including email, social media, banking, and other crucial services.
- Use a strong password: Your password is still your first line of defense. Use a strong, unique password for each account.
- Store backup codes securely: Most services provide backup codes that you can use if you lose access to your 2FA app. Store these codes offline in a secure location, such as a password manager or a physical safe.
- Keep your devices updated: Regularly update your devices’ operating systems and applications to ensure you have the latest security patches.
- Be vigilant against phishing: Phishing attacks are still a significant threat. Always verify the URL of the website you’re visiting before entering your credentials.
- Regularly review your connected devices: Check the security settings of your accounts and remove any unfamiliar or suspicious devices.
The Future of 2FA: Proton’s Vision
Proton’s 2FA app is not a static product. Proton has a clear vision for the future of 2FA and is continuously working on improving its security, functionality, and user experience.
Ongoing Development and Enhancements
Expect regular updates and new features to be released. Proton is known for its iterative development process, where features and functionalities are added over time based on user feedback and evolving security needs.
Potential Future Features
- Support for Hardware Security Keys: While the app currently relies on TOTP, Proton might integrate support for hardware security keys (like YubiKey) for even stronger security.
- Advanced Recovery Options: Refining and expanding recovery options is essential.
- Enhanced User Interface: Expect improvements to the interface based on feedback and user testing.
Why Proton’s 2FA App Should Be Your New Security Standard
In a digital landscape where security is paramount, choosing the right tools is crucial. Proton’s 2FA app distinguishes itself by offering a combination of robust security, user-friendly design, and unwavering commitment to privacy. While Microsoft Authenticator is a functional solution, Proton’s approach is fundamentally superior for several key reasons:
- End-to-End Encryption: This is the most important differentiator. Your 2FA secrets are always protected, even if Proton’s servers are compromised.
- Privacy-Focused Design: Proton prioritizes your privacy, minimizing data collection.
- Seamless Integration: Integration with the Proton ecosystem is a significant advantage if you already use other Proton services.
- Open Source Principles: The open-source nature allows for transparency and community scrutiny.
- Ease of Use: The app is easy to set up and use.
Conclusion: Embracing a More Secure Digital Future
The emergence of Proton’s 2FA app marks a pivotal moment in online security. It gives users a robust and secure alternative to the current market leaders. By prioritizing end-to-end encryption and a commitment to user privacy, Proton has created a 2FA solution that aligns perfectly with the needs of the modern digital citizen. Switching to Proton’s 2FA app means you’re not just protecting your accounts; you’re also embracing a future where privacy and security are paramount. In the constant battle for online security, the future is looking bright, and Proton is leading the way. We at revWhiteShadow strongly encourage our readers to make the switch and experience the peace of mind that comes with using a truly secure 2FA solution. Make the decision today and take a critical step in fortifying your online presence.